SEOUL, July 25 (AJP) - A research team from South Korea has identified a critical security flaw that allows a single wireless packet to crash a smartphone’s cellular modem. The vulnerability affects a broad range of devices and highlights long-standing security gaps in the modem layer.
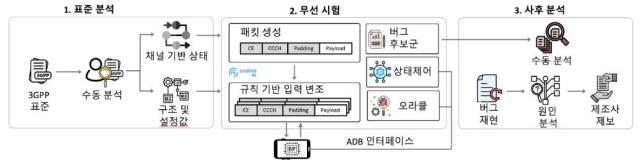
The project was led by Kim Yong-dae, professor at KAIST, and Park Cheol-jun, professor at Kyung Hee University. The team developed a custom testing framework called LLFuzz to examine the lower layers of mobile communication protocols. Unlike the upper layers, which are typically encrypted and authenticated, these lower layers can accept external signals with minimal filtering.
Using LLFuzz, the researchers tested 15 commercial smartphones from manufacturers including Apple, Samsung, Google, and Xiaomi. They discovered 11 previously unknown vulnerabilities. Seven of them have been assigned CVE identifiers and patched by vendors. The remaining four have not yet been disclosed.
In a demonstration, the team showed how a malformed packet, transmitted from a laptop using a software-defined radio, could instantly disable a phone’s modem. A test video captured a phone streaming data at 23 megabytes per second before abruptly freezing and losing all signal after receiving the packet.
"Smartphone baseband layers can accept arbitrary external signals without authentication, which introduces systemic risk," Kim Yong-dae said. "This research shows that standardization in modem security testing is no longer optional."
The vulnerabilities were found in modem components known as RLC, MAC, PDCP, and PHY. These layers handle wireless signaling, error correction, and data transmission. Because they are not protected by encryption or authentication, they are susceptible to input from outside sources.
Affected chips include over 90 from Qualcomm, around 80 from MediaTek, Samsung’s Exynos 2400 and 5400, and Apple devices using Qualcomm hardware. These modems are used not only in flagship smartphones but also in tablets, smartwatches, and low-cost IoT devices.
The LLFuzz system compares device behavior against 3GPP telecom standards to detect inconsistencies caused by implementation flaws. The researchers believe that the lack of standardized security testing for abnormal packet behavior is a key reason such issues have gone unnoticed.
"Even leading manufacturers have overlooked this area," Kim said. "Our work highlights the dangers of deploying technologies that have not undergone sufficient scrutiny."
The research will be presented in August at USENIX Security 2025, a leading international conference in cybersecurity. The paper, titled LLFuzz: An Over-the-Air Dynamic Testing Framework for Cellular Baseband Lower Layers, is authored by KAIST doctoral student Tuan Dinh Hoang, along with researchers from KAIST and Kyung Hee University. The team plans to release the LLFuzz tool as open-source software.
Early tests on 5G baseband chips using the same framework have already uncovered two additional vulnerabilities. The researchers are continuing to expand the tool and explore broader testing strategies for both LTE and 5G systems.
The project was funded by South Korea’s Ministry of Science and ICT and the Institute of Information and Communications Technology Planning and Evaluation.
Copyright ⓒ Aju Press All rights reserved.




